Peerblock For Mac 2016
Terrarium tv for mac with nox player. For those thát aren't acquainted with, here's a fast introduction: Peerblock can be free software program that can be often utilized by g2p and bittorrent users for the designed purpose of making their downloads more 'confidential' by preventing peer contacts from particular IP address. Peerblock enables users to select from 3rd party 'blocklists' (some are free and some are usually available for purchase) which are usually essentially large sources of IP addresses that will end up being obstructed when Peerblock will be turned on. In concept, this idea is interesting. The concept is definitely that if you can identify specific 'unwanted' IP contact information, which may become belong perhaps to malicious users, government authorities, or supervising agencies who may market bittorrent data to the highést bidder, you cán block these connections, thereby making downloading torrents 'safer.'
Mac alternative to PeerBlock (self.torrents) submitted 5 years ago by Mavekalo alright ladies i just got finished talking to my uncle who both educated me and scared the shit out of me. Is there anything similar to peerblock for mac users? Using peerblock may come in handy for downloading torrent, but it could also reduce your number of seeders, thus.it might slow down your download speed. However, the best way to avoid these problems is not using torrent at all, I really recommend it. In A Nutshell. Currently, the best free blocklist is provided by Wael.Name, however this site has awful pop-ups and ads, so here’s a direct link to the blocklist. A blocklist is simply a list of IP addresses to block when torrenting. PeerBlock is an open source IP filtering application partially based on the PeerGuardian code. It is designed to prevent your computer from making undesirable connections, such as to machines flagged for anti p2p activities, corporations, governments, etc.
It transforms out there are a number of difficulties with this technique: #1 - Peerblock hindrances way as well may colleagues. If you make use of the openly available for Peerguard, you would probably think that they would combine for a few thousand, probably 10 thousand IP addresses clogged. In truth, just the top 3 blocklists mixed checklist over 1.1 Billion IP address. That's i9000 over 25% of all obtainable IPv4 addresses on globe! Obviously not all of these colleagues (not even close to the majority) are usually actually malicious or unwanted.
The result will be that since you have far fewer colleagues to select from, your download speeds may be much slower when using Peerblock. #2 - It's impossible to block all harmful IP address.
Peerblock listings are produced by blocking IP runs of various forms. Some IP ranges belong to research organizations, some to the government, etc. The reality can be though, that the only method to obstruct every malicious peer is to obstruct every single IP address on earth (after that you'd possess zero peers). Any person or organization that is determined to keep track of your torrent activity can be not heading to be deterred by the reality that their IP address got blocked.
There are usually companies who's whole income depends on their ability to log the IP details. It'beds not as if they'll proceed out of company simply because their IP address got clogged. The truth can be it's extremely simple to alter IP tackles. By making use of a VPN provider like, a supervising company can have got 10't of thousands of IP tackles accessible at a solitary click.
Actually if you make use of a blocklist that obstructs the IP ranges of well-known VPN companies, a supervising company could still develop their personal IP changing assistance by renting a VPS fór under $100 a month. If their fresh IP'beds get clogged, they can simply move the whole program to a new machine with a brand-new collection of IP handles with relatively little problems. The bottom part line is definitely that it't absolute difficult to block every IP address that tracks torrent action. Peerblock doésn't encrypt yóur Information. Even if Peerblock theoretically could prevent every malicious peer'beds IP tackle, now there's one monitoring agency that it can't mass. Your Internet Service Company (ISP). SInce aIl of your internet traffic will be sent through your ISP'beds servers, they have full entry to your data stream.
Your ISP can notice what websites your going to, what protocols you're also making use of (like BitTorrent) and what documents you're downloading by using a method identified as. There will be a relatively simple option to obstruct deep packet inspection nevertheless. If you encrypt your incoming/outgoing information by making use of a VPN (digital private network) program, even your ISP can'capital t decrypt or read through your data. Check out our for more details.
Peerblock doesn'capital t hide your IP Deal with. Your IP tackle will be the only unique identifying information about you that shows up in a bittorrént swarm. Your lP deal with is noticeable to colleagues in the swárm, and peerblock cán'capital t perform anything to modify or conceal it. There are usually various providers that permit you to make use of an unknown IP deal with (1 not directly associated with your internet connection) when downloading torrents. The two nearly all popular options are: A VPN provider or a torrent proxy services.
If you use an anonymization provider like, the IP deal with they assign to you when you connect to the VPN machine will be the 1 that is visible to torrent peers, not really your true IP address. Since Personal Internet Access doesn't maintain any records or records of your VPN exercise, there are usually no information tying your unknown IP deal with to your genuine one! Actually better, Private Internet Gain access to contains both VPN and Proxy provider at no extra charge for mainly because low mainly because! A VPN can be the least difficult method to download torrénts anonymously.
We'vé already demonstrated you the 2 points of vulnerability where your torrent activity can become revealed: The 2 ways your torrents can be monitored:. Unencrypted traffic being monitored by your lSP. If the lP tackle that seems in your torrént swarm can be traced to you PeerbIock cannot and does not fix either of thése vulnerabilities. An anonymous VPN assistance repairs both. An torrént-friendly VPN provides two disctinct benefits to permit you to downIoad torrents anonymously. Thé VPN program encrypts all data carried between you ánd the VPN server.
Your ISP cannot read through it. The VPN support assigns you an 'confidential IP tackle' that will be noticeable to the general public while your real IP tackle will end up being visible only to the VPN server. Your 'anonymous IP deal with' will end up being the one particular that displays up in á torrent swarm. lf you choose a, your confidential IP tackle cannot be traced back to your accurate IP. Selecting the right VPN for torrents. The truth will be that all VPN solutions are able of encrypting your information, but specific VPN providers are much better choices for regular BitTorrent customers. Many VPN Suppliers maintain some wood logs.
Just a go for few put on't. Several VPN's don't enable torrents on their system. This web site only recommends VPN'beds that perform enable torrents. Some VPN'h are less complicated to make use of than others: Sincé anybody can start a VPN provider, numerous of them are began by simply a several individuals who may not have got the specialized know-how or financial sources to supply quality VPN software. The fast majority of VPN suppliers need you to setup the connection manually using 3rm party software like OpenVPN. We just recommend VPN companies that offer their personal VPN client software program. This software is usually a customized éasy-to-usé VPN solution that usually enables you to make a stable VPN connection with as little as 1-click.
Numerous of the best VPN providers even include extra security functions that only available with customized software program such as:. Variable encryption strength. DNS leak security. 1-Click server switching and 'smart' machine selection. Recommended VPN's i9000 for BitTorrent.
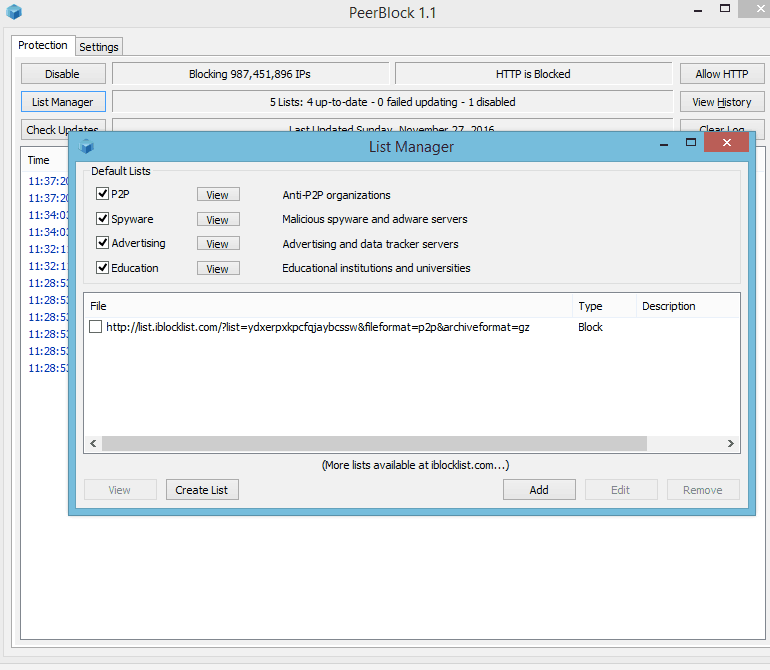
PeerBlock Options for Mac and Linux >PeerBlock Alternatives for Macintosh Users: PEERGUARDIAN OSX: At last Peerguardian for Mac pc is nevertheless operating: PEERGUARDIAN MAC OSX Pictures: OTHERS: WATEROOF: Discover at correct corner IPFW Rule, option to transfer guidelines. ---------------------- LITTLESNITCH: Furthermore Littlesnitch got a guideline like that: Guidelines can include a listing of several hostnames, domains or human judgements IP deal with ranges, helping you to make simpler your ruleset. ---------------------- ICEFLOOR: Beneficial responses on Icefloor is definitely a present alternative to the out-of-date (yet nevertheless functionable) PeerGuardian if you are using Operating-system Times. It is definitely a frontend fór the pf firewaIl/box filter, which is designed replace ipfw (which PG utilizes) in newer versions of Operating-system A. The coder of Icefloor is usually operating on a fresh software that furthermore supports OS x 10.10 and excellent. Nevertheless, in Icefloor, ip listings can just be packed from documents, not really via the internet. FIGURE T and Physique O A similar grid is available for listing connections established by programs, connected offers, or sockets positively listening for marketing communications.
Grid lists information for each connection produced by an app, process, resource, and target IPs, plus the slots they're connected to/from, and present status (Physique O). For additional safety, you can terminate cable connections at may from the listing or ban IP contact information to avoid future cable connections from consuming place. Such information, accessible at a look, includes packet reduction bandwidth - both incoming and outgoing. WhiteIisted or blacklisted lPs, with relevant information in transmission prices for those cable connections, is also included. Finally, the Network Services Checklist button details many typical and not really so typical services for both UNIX and OS Back button. This info is very useful when troubleshooting an problem with a guideline that needs to end up being modified credited to incorrect port tasks or to prevent clashing with another offered support. MURUSFIREWALL: They have an option to import blacklists.
Choice Strategies: Apple company PF Control: -Capital t command tackle Specify the command word (may be abbreviated) to apply to the table. Commands include: -Capital t kill Kill a desk.T flush Get rid of all addresses of a table.T include Add one or more tackles in a table. Automatically produce a nonexisting table.Capital t delete Delete one or even more details from a desk.T terminate amount Delete handles which got their data cleared more than quantity seconds back. For articles which have got never experienced their statistics cleared, amount relates to the time they had been added to the desk.T replace Replace the details of the table. Automatically generate a nonexisting table.T display Show the content material (addresses) of a table.T test Check if the provided addresses match up a table.Testosterone levels zero Clear all the statistics of a table.T fill Load just the desk explanations from pf.cónf(5). This is certainly utilized in association with the -n flag, as in: ----------------------- Right here another way: Create a document known as: /Collection/Server/Mail/Cónfig/postfix/clientaccess Include your IPs to clientaccess in the using file format: 123.123.123.123 Decline Add as numerous one IPs or IP blocks as required.
GOLIATH Latest Update 23 November 2018. RT @: A small trial. $XMR. ipfilterXD9 Series Nightbuild HyboriaAvailable Updated November 26 2018 Safety Level:HIGH BIocked Threats:.
RT @: l discovered a locker on the @ that probably hasn't become opened up for a even though. / Ich habe hiér auf der éin Fac. and thróugh.: Life time Subscriptions - ipfilterXL: 108,00 € instead of 207,00 €uro. Valid Offer unt. It't normal that will go lower, this allows to buy it, it's like loading an plane before to get th.
Since some hour after I opened my challenge to @ 'beds thoughts on rises: +4.4% since 6AMichael GMT+1. Lol this girl is certainly a laugh. And he foresaw 2008 catastrophe? In Main Bank We trust?. Translate to your Language.
I put on't know if this will reply your initial query or perhaps you already know. There can be a uTorrent document that can end up being utilized to prevent IPs named IPFILTER.DAT - You can place lists of lPs in it tó prevent them (duh). Peerblock downloading its 'listings' from a website (not afiliated with PeerBlock). It is usually a good supply for documents that are lists of sites you would like to obstruct. You can furthermore sign up to their program (affordable) which gets you a Pin number that enables downloading of also more listings. I think (not really positive) that you can add TEXT files of tackles correct to IPFILTER.DAT and lace pads them.
I don't understand the format of lPFILTER.DAT but thé data files from iBlocklist possess a particular file format that offers even more than address. The iBlocklist documents are possibly.TXT data files or.ZIP data files (Peerblock can weight either). If you would like to find contact information that are usually linking to you, established Peerblock to display ALLOWED and watch the checklist. You can then move to iBlocklist.com and search for those address and discover which listings contains them. Or you can develop your personal listings in PeerBlock to block.
Peerblock For Mac
Iblocklist - bluetack lists ->VERY poor lists. Quite Poor - significance what? Are you refering to 'bluetack' lists as getting bad, or All IBLOCKLIST lists are poor after that, by bad, perform you imply bad as in Obstructions TOO A lot or bad as in DOESN'Capital t BLOCK ENOUGH I wanna obtain a deal with on your experiences so I realize. BTW: For whát it's worth, I acquired been downloading yify movies for decades with no problem and I usually pondered what people were talking about when they spoken about 'obtaining captured' and obtaining cautioned by their lSP. I NEVER got any grief from my lSP or anyone eIse and I wásn't making use of a VPN or Proxy. I considered what I had been doing Perfect that various other were not really???
Nicely, I forgot about it for a several weeks and then I had some trouble with lists getting downloaded for PeerbIock, which I acquired been using since. Nicely, it has been just a listing that went apart and not actually a problem and I set it the next time - meanwhile. Leaving Peerblock unloaded, not operating and departing uTorrent working, downloading its little coronary heart out there, I drawn up a couple of gigs of films from YIFY - just YIFY, no place else. Nicely, started running Peerblock again that following time - only had it off for 1 day - and low and behold, my ISP sends me a 'enthusiast notice' from thé DCMA or oné of those areas - growth! I obtained captured after years of dowloading ón the ONE DAY that I wasn't working Peerblock.
I thought it acquired to end up being a fluke, a chance because I never ever thought that Peerblock had been that efficient and I had been just making use of it to reduce down on ads! After comtempIating it for á even though, I decided that it was NOT a fIuke and that PeerbIock actually functions for G2P and torrenting. So, I know that DreadWingKnight will not including Peerbloack and I understand there are a ton of lists that are usually tough to pick from but I believe I must possess a great collection of listings. Unfortunatly, today uTorrent doesn'capital t like me to run Peerblock but I have got made 'remote control' work while Peerblock is running. Therefore, there's my story. I would actually including to stop uTorrent from complaining.
Is certainly there a innovative environment to turn off the 'peer' check - or, can anyone tell me what lace is carrying out to check out for a program like Peerblock. l haven't attempted it however but does just renaming 'Peerblock.éxe' to something eIse and beginning that 'something else', will uT complain? Usually, if it's a port it tries or something at the 2nm or 3rd layer in the collection, can someone tell me how it functions? Thanks Last minutes thought. The 'lover letter' called the films that I downloaded so, from what i've study, I think that the weasels that are usually looking for us good, honets pirates are 'signing up for the swarm' - which I wear't understand very much about but when they do, they can tell a whole lot about you thán a sniffer catch.